TL/DR Summary:
- Nation-state APT Midnight Blizzard / Nobelium compromises Microsoft with simple password spray in legacy environment.
- Senior leader e-mails compromised; no customers impacted.
- APT’s objective seems to have been gathering intel on what Microsoft knew about them (Midnight Blizzard).
- “What not to do”: The incident highlights several cybersecurity oversights at Microsoft, including MFA implementation and legacy system management.
- This attack is embarrassing given how often MS writes posts urging organizations to use MFA…
A Blizzard in January
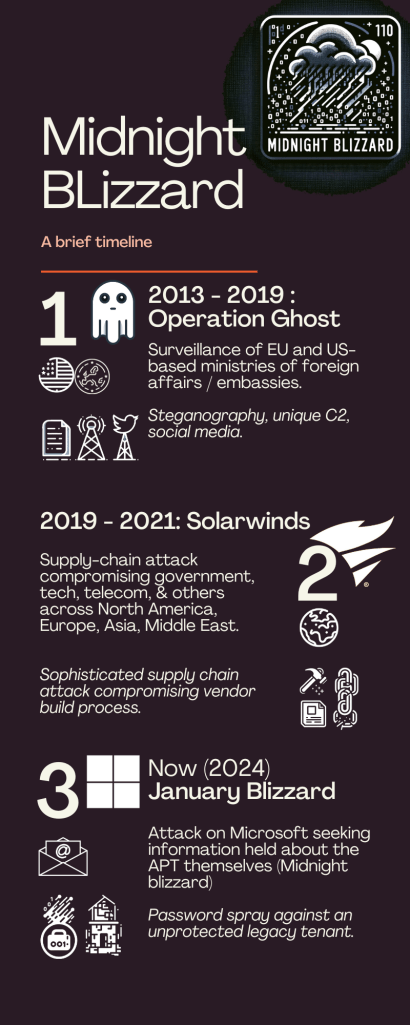
Cybersecurity isn’t just for the “little guys”… This winter kicks off with Microsoft reporting that it found itself in the icy grip of Midnight Blizzard, a notorious Russian state-sponsored hacking group, also known as ATP29, Nobelium, and a host of other names. You may remember Midnight Blizzard them from a few years back – the SolarWinds supply-chain incident (MITRE).
On the other side of this, while Microsoft has come a long way since the “Wild West” days of the 90s, this breach throws a spotlight on lingering vulnerabilities and exposes some uncomfortable truths about the state of corporate cyber defense.
Sophisticated Objectives, Simple Techniques
The attack’s success, facilitated by a simple password spray, raises questions about Microsoft’s adherence to its own advocated security practices, particularly the use of Multi-Factor Authentication (MFA). This oversight is particularly ironic for Microsoft, a proponent of robust security measures including MFA.
From this initial account compromise, Midnight Blizzard infiltrated Microsoft’s internal systems, specifically targeting the email accounts of senior leaders and executives – a chilling prospect for any company, let alone a tech giant. More specifically, the attackers exfiltrated emails and attachments where the group itself (Midnight Blizzard) was mentioned – suggesting their objective was to understand what intel, theories, and strategies the tech and security giant might hold about them.
While Microsoft quickly contained the attack and determined that “The attack was not the result of a vulnerability in Microsoft products or services” and that no customer data was involved, this incident still raises a number of questions.
Legacy Systems cast a long shadow
Equally interesting, Microsoft’s disclosed the compromise came through “a legacy non-production test tenant account” – underscoring the risks associated with inadequately managed legacy systems. In particular, it raises questions about gaps in configuration management, threat hunting, and internal audit.

Aside from the apparently lax security settings on the compromised tenant, one would also question how a “non-production test” account would facilitate compromise of actual production e-mail accounts – suggesting the environment may not have been well-isolated from core Microsoft resources and/or contained replicated secure information from production.
We all have “legacy” systems in our environments at some time or other – this attack highlights just how dangerous they can be when neglected.
Learning from the Chill

While the Microsoft attack raises concerns, it also offers valuable lessons for businesses of all sizes:
- MFA is non-negotiable. Implement it everywhere, no exceptions. This simple step could have thwarted this entire attack, as well as many recent high-profile attacks.
- Don’t let legacy haunt you. Audit and secure your “old” environments. Sunset them if possible or ensure they’re isolated and locked down like Fort Knox.
- Validate Configurations and controls. Ensure all environments, regardless of purpose, adhere to security & configuration protocols. Where exceptions are truly necessary, make them thoughtfully, “in-process”, and periodically audit and revisit those decisions.
- Think twice before connecting. Is production data really needed in non-essential environments? What about cross-environment connectivity / access? Minimize potential attack vectors.
The Microsoft hack is a reminder that no one is immune to cyberattacks. All organizations, be they tech giant or start-up, need to consistently question design decisions, enforce policies and controls, review how real environments measure up to standards, and evolve their security measures.
Ultimately this incident reinforces that consistency and defense-in-depth are crucial – attackers only need to be “lucky” once, while defenders must execute correctly every time. Learn from Microsoft’s missteps, don’t be caught in the next “blizzard”.


Leave a comment