NOTE: This post is a wrap up of a preceding post and follow-up covering the September 2023 MGM ransomware incident.
After a release late last week, reported on multiple major news providers, we now have a clearer picture of the September incident widely believed to be a major ransomware attack on MGM. MGM’s 8-K SEC filing and data breach notification offer detailed insights. Here’s a rundown.
TL / DR: Summary
- Hack will cost MGM ~$110 mm, primarily lost revenue. Insurance is expected to cover it.
- Expect no major changes from MGM – this is a small sum for them.
- Uknown number of customers’ data was breached, potentially many thousands. Affected individuals should follow ID-theft response best practices.
- MGM scores a D in readiness, a C in response based on the author’s assessment.
- Key Lessons for Defenders
- An ounce of prevention – fundamentals count – by all appearances better security training and MFA could have prevented all of this.
- This is an excellent case study in justifying a security budget.
Financial implications to MGM – Very Little
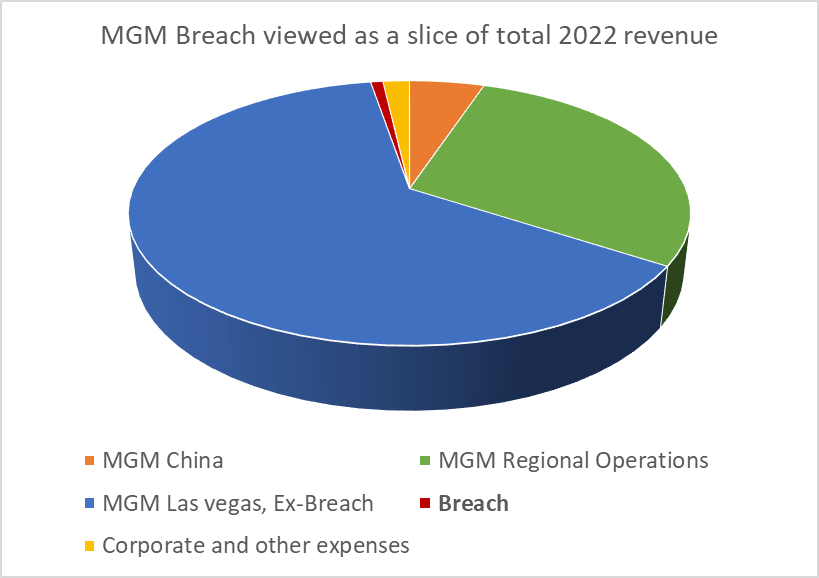
$110 million sounds like a vast sum to most of us. However, in the context of MGM Resorts International’s over $13 billion in annual revenue (~$8.4 billion of which from Las Vegas interests), it’s just drops in a bucket. (data sourced from MGM’s own annual reports)
More interesting is the breakdown in the cost incurred. The vast majority – ~$100 million, is in hotel (and related service) revenue. Only $10 million was actually spent on cyber response, including consultancy and legal fees. MGM further noted it expected the entire cost to be borne by its cybersecurity insurance program. (source: 8-K SEC filing)
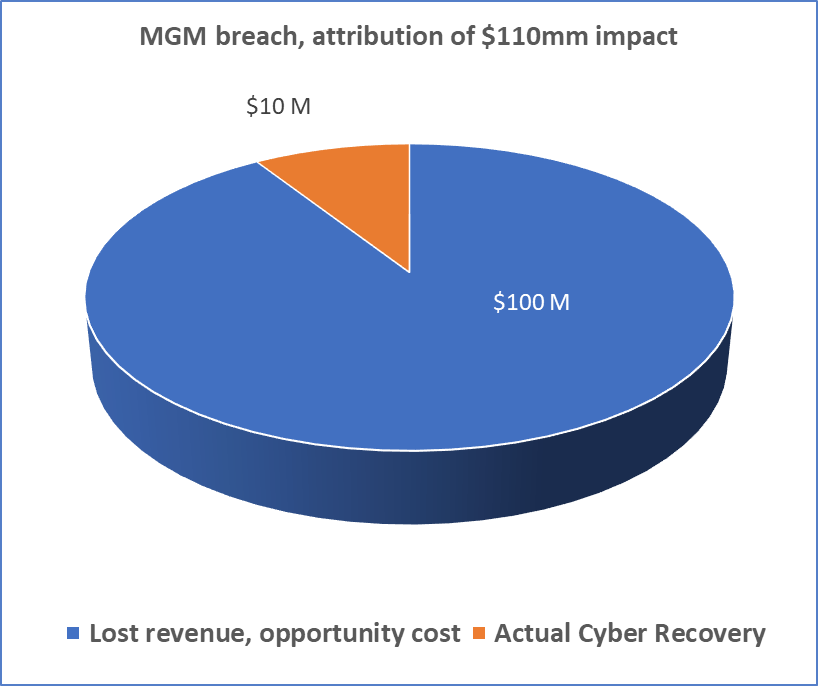
Given the tiny fraction of MGM’s earnings this represents and the short attention span of the public writ large (MGM expects all revenue to be “back to normal” by November), we’re unlikely to see any major change at the corporate level despite heavy press coverage and the mockery from the claimed attackers.
Customer Impact: Name, License, and … social security?
MGM’s Data Breach notification reveals the consumer victim side to this. For the unknown thousands(?) impacted, the beach included:
- Name
- Contact Information
- Gender
- Date of Birth
- Driver’s License numbers
- For an unspecified subset – Social Security and / or passport numbers.
Scope: Just how many people were impacted?
MGM has thus far in all forums declined to comment on the specific numbers of individuals impacted, though they clarified guests from 2019 and earlier were impacted. MGM boasts 10 million guests per year – so this could be a big number.
Moreover, MGM says “some” customers “may” have had social security or passport information compromised – offering no other specifics and making it hard to assess scope as an outsider.
Realistic ramifications for impacted individuals
The repercussions for those affected vary. Social Security Numbers, for that subset, are the classic “golden ticket” for identity theft (see also my initial post and soon-to be published sequel on my own experiences there). For those individuals, speedy kickoff of recovery including engaging the FTC, filing a police report, placing a fraud alert and possibly freezing their credit are all “best practice” responses.
A driver’s license might seem like a small problem by comparison, but still offers a criminal many options:
- Procure services in a victim’s name – e.g. purchase some banking products, purchase firearms, to name a few.
- Commit Crimes in a victim’s name – a driver’s license is the standard form of identification collected by law enforcement to establish identity. Anything from speeding tickets to larceny or more could have all legal consequences associated with a victim whose ID number was used.
- Create one or more fake identities– which could be used to procure services, or simply be resold for profit. Smart criminals can also use a drivers’ license as a springboard for research to develop a more complete picture.
- Mail Fraud – with information like a name, address, and signature, it’s easy to send packages (of drugs or other contraband, for example) “as” another person. Or to request mail redirection to a new address – intercepting a victim’s bank and credit card statements, etc.
- Medical Fraud – lesser medical services like getting prescription medication can be secured with the information available on a drivers’ license.

Suffice to say, many of the same response activities appropriate to a social security theft are appropriate for victims of a simple driver’s license theft.
Final Analysis: Lessons to be learned
MGM’s readiness: D (Author’s opinion)
Protection measures like user training and multi-factor authentication (MFA) were glaringly absent, leading to vulnerabilities. These sorts of protections are called for by all major security frameworks – e.g. NIST-CSF – and are basic protections whose lack comes up time and time again in breach reports.
Although detection occurred reasonably (in line with averages), it was far from top-tier.
MGM’s response: C (Author’s opinion)
MGM’s response was average. They appeared to lever external experts in response (A best practice) and it’s notable they seemingly opted against paying the ransom – a contrast to the other recent Vegas hack with Caesar’s. MGM’s stance on this was good – paying out is no guarantee of threat actor cooperation, and doing so encourages further cybercrime.
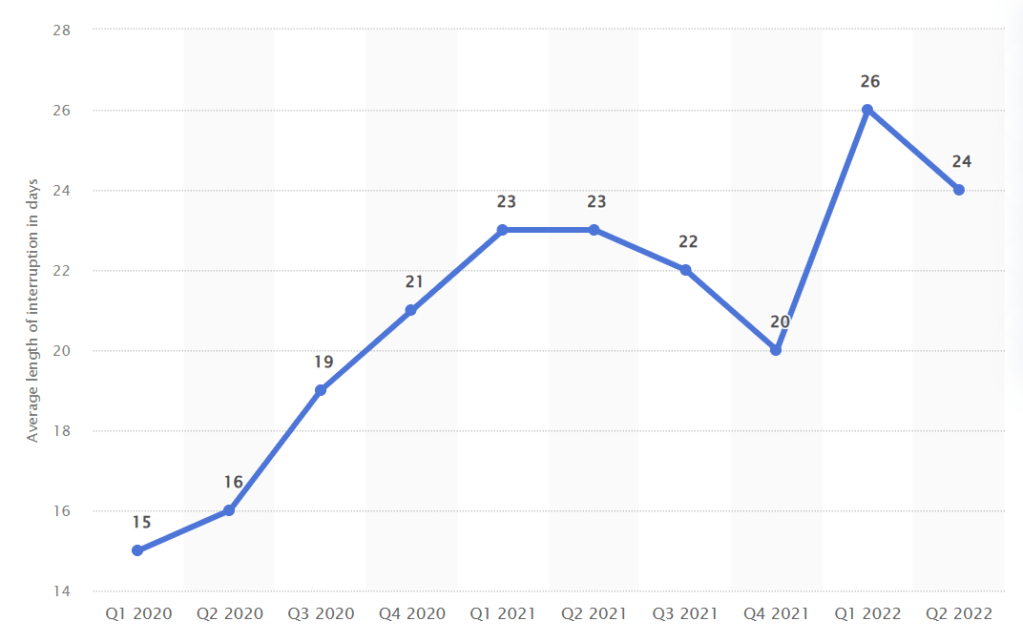
And while we have little insight into the overall recovery effort, the ~20 days it took is in line with trends as reported by data company Statista.
For Consumers
There is not much for the consumer to learn here – most of the fault here is in company security stance. For most, limiting their digital footprint and monitoring their credit and personal data are the biggest takeaways. The prior reduces the probability of being impacted in a breach, the latter the detection and response time to one.
For Other Defenders
For non-MGM defenders, the key takeaway is that security fundamentals go a long way. Employee security training is often neglected, and often implicated as key in many realized breaches. Likewise, proper use of MFA can help shore up lapses in training or other controls. From what we know, either or both of these could have prevented this instance.
Finally, this is an excellent case study of the old adage about an “an ounce of prevention.” With a cost of ~$110 million for this instance, it would be easy to make a case for implementing one or both of the above solutions, even should they cost one’s organization in the millions. Although insurance looks like it will cover this case, it won’t always, and prevention also sidesteps any harder-to-quantify reputational risk (this is, after all, the 2nd major breach at MGM in 3 years…).


Leave a comment