ESET Group researchers reported Friday that the Lazarus Group, suspected North Korean threat actor, has been linked to a sophisticated attack targeting Spanish aerospace engineers. The incident showcases the ongoing evolution of both Lazarus’s targets and techniques.
TLDR / Summary
- Lazarus Group members impersonated tech recruiters to trick targets into downloading an ISO package with a set of “coding test materials” – and a malicious payload.
- Running those materials triggers a DLL side-load, which would in turn load a simple HTTPS downloader (dubbed “NickelLoader” by ESET)
- This served as a gateway for Lazarus to push two more sophisticated RATs (Remote Access Trojan) to the target’s system – simplified variant of Lazarus’s well-known BlindingCan, and a new RAT – LightlessCan.
- LightlessCan is particularly interesting, as it appears to have been engineered to be far harder to detect than its predecessor.
- Though the motives of the attack are unknown, the choice of targets suggests espionage and tech theft rather than pure moneymaking.
Initial Access
Things started with Lazarus members masquerading as Meta recruiters on LinkedIn. Anyone who’s used that platform for any length of time has probably seen MANY of these kinds of unsolicited reach-outs firsthand, making the attack less conspicuous.
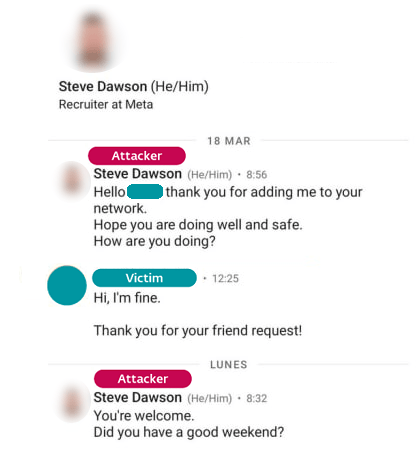
After expressing interest in a further evaluation of the “candidate”, the attackers would direct the engineers to download ISOs packed with interview tasks from a third-party cloud storage. Once victims executed those materials, the payload within would start the full attack.
If ever one needed a real-world example of why not to run unverified executables from the internet, here it is.
The whole initial access chain looked something like this:
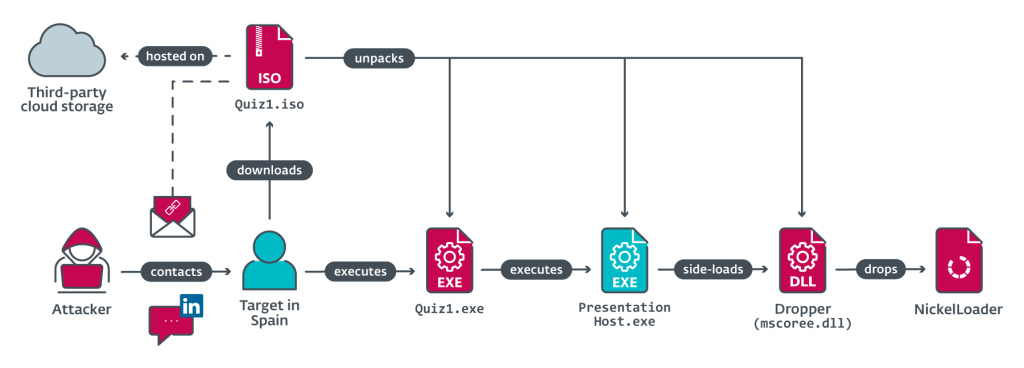
Payload
I won’t get too deep into the technical details here, for those inclined check out ESET Group’s excellent report detailing the nitty gritty. They have a full functional analysis of the malware, all binaries involved, etc.
In essence, triggering the attack payload side-loaded a DLL onto the system, which in dropped a simple HTTPS downloader (dubbed NickelLoader by ESET) on the system.
Lazarus would then use this to deliver the actual main payload, two RATs (remote access trojans) – a stripped-down version of their well-known BlindingCan, dubbed “miniBlindingCan” by ESET, and an as-to-now unseen RAT called LightlessCan – which seems to be a successor to BlindingCan.
Of interest in LightlessCan’s dozens of built in functions are a number mimicking the function of built in windows OS commands, but running entirely within the malware itself (and not through the system console). This could be bad news for EDR and monitoring in general, as standard windows system logs of these commands would not exist – making LightLessCan much stealthier than its predecessor.
There’s a lot more to be said here – such as an alternate, more complex delivery method for LightLessCan, as well as interesting attributes of the RAT itself (e.g. encrypted local storage of some files) – Check out the ESET report for all of this.
Objectives and Conclusion
Interestingly, though Lazarus Group is perhaps best known for fundraising via ransomware, crypto theft, and other attacks (stealing an estimated several billion dollars since operations began ~2007), the motive here likely wasn’t a cash grab given the targets. More probably, the goal here was to get access for potential technology or research theft, as a staging point for further activity, or other espionage. Note the above is my own speculation based on the known facts – readers are encouraged to draw their own conclusions.
Over the last few years North-Korea linked APTs have been expanding their targets and techniques, and this latest attack bears a lot of similarities to the previous Operation Dream Job / Operation Interceptor and could be considered a continuation of that campaign (though depending on if you’re asking MITRE or ESET, those campaigns either closed or never stopped).
The new LightlessCan RAT is probably the most technically interesting part of the attack, and perhaps most worrisome. Its capability to bypass system logging around some core OS commands, commonly used by EDR and SIEM platforms, signifies another step in the ongoing cyber-attack and defense arms race.


Leave a comment